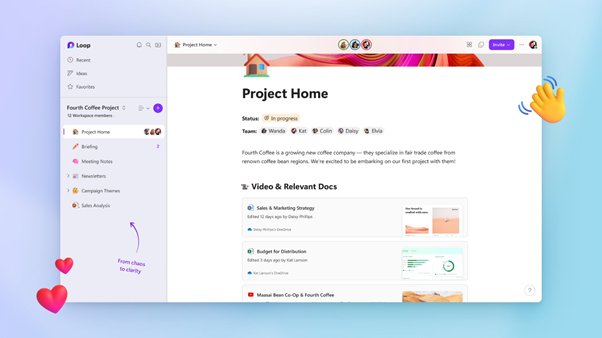
What would be the difference to your business of not having to spend thousands of dollars for new IT hardware? Ultra IT offer a leasing option on a “Managed Device Agreement” as a way for our Northland businesses to keep up with the ever-evolving landscape of information technology.
The leasing of IT hardware is becoming a very attractive alternative to outright purchasing, as it offers a range of advantages that can significantly benefit organizations, from startups to established businesses.
In this blog, we’ll explore the various advantages of the Managed Device Agreement and how it can contribute to the success and growth of your business.
Recently one of our customers was faced with an $80,000 capital outlay for new hardware. We discussed the many benefits of the Managed Device agreement and our client was so happy to be able to access new equipment without this massive outlay.
Cost-Efficiency:
One of the primary advantages of leasing IT hardware is the immediate cost savings it provides. Traditional purchasing involves a substantial upfront investment, tying up valuable capital that could be used for other critical aspects of the business. Leasing allows businesses to access the latest technology without the burden of a hefty initial expenditure. This predictable monthly expense structure makes budgeting more straightforward and allows organizations to allocate funds more strategically.
Technology Refresh:
The pace of technological advancement is relentless. By leasing IT hardware, businesses can stay at the forefront of innovation without worrying about the rapid depreciation of assets. Leasing agreements often include provisions for technology upgrades, enabling organizations to seamlessly transition to newer, more advanced equipment at the end of the lease term. This ensures that businesses always have access to the latest tools and technologies, fostering a competitive edge in the market.
Flexibility and Scalability:
Business needs are dynamic, and the ability to scale operations efficiently is crucial. Leasing provides the flexibility to adjust the scale of IT infrastructure according to the organization’s evolving requirements. Whether it’s expanding operations, accommodating seasonal fluctuations, or downsizing during economic challenges, leasing allows businesses to scale their IT infrastructure up or down without the complexities associated with asset ownership.
Reduced Maintenance Costs:
Leasing IT hardware often includes maintenance and support services as part of the agreement. This can result in significant cost savings for businesses, as they don’t have to bear the burden of repairing or maintaining the equipment. Instead, the leasing company assumes responsibility for ensuring that the hardware remains in optimal working condition. This not only reduces operational hassles but also provides peace of mind, allowing organizations to focus on their core competencies.
Tax Benefits:
Leasing IT hardware can have favorable tax implications for businesses. Lease payments are typically considered operational expenses, which can be deducted from taxable income. This contrasts with the depreciation of purchased assets, which may yield tax benefits but often over a more extended period. Businesses should consult with tax professionals to understand the specific advantages and implications based on their jurisdiction and financial structure.
Risk Mitigation:
The technology landscape is fraught with uncertainties, ranging from hardware obsolescence to unforeseen market changes. Leasing mitigates these risks by transferring the burden of technological and market fluctuations to the leasing company. This ensures that businesses are not saddled with outdated or ineffective equipment, providing a safety net against unforeseen challenges.
Conclusion:
Leasing IT hardware emerges as a strategic and cost-effective approach for businesses aiming to navigate the complexities of the modern technological landscape. The advantages of cost-efficiency, technology refresh, flexibility, reduced maintenance costs, tax benefits, and risk mitigation collectively position leasing as a compelling option for organizations seeking to optimize their IT infrastructure. By embracing this model, businesses can not only streamline their operations but also position themselves for sustained success in an ever-evolving digital world.
We have written previous articles about the advantages of a Managed Service Plan for your business that may be of interest too.
For more information contact Ultra IT to discuss your business requirements.